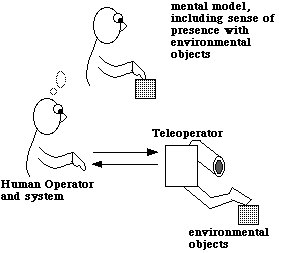

There are many applications for a tight control loop. This is generally desirable where the outcome of a particular action must be assured. Telesurgery, for example, is one such application where momentary loss of control could result in disastrous consequences.
There is however another class of application where tight control is not the critical measure of success and might even be undesirable. For example, remote security cameras in locals like bus terminals or train stations typically provide very noisy images and allow only intermittent control (if any), yet still provide sufficient information for a human operator to feel confident in their function and make use of their information.
We selected a dog's leash as a metaphor for loose control of a remote device much in the same way that one maintains loose control of a dog while it is being walked. The dog is controlled through tugs on its leash yet the dog is free to do what it wishes within the restrictions imposed by its tether. Controlled by a leash dogs are used as aids for the blind, as a means for detecting illicit narcotics and a myriad of other applications--short of surgery.
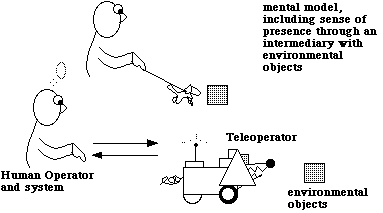
We adopted this metaphor because of the way a communication media such as the WWW work. Our device would be controlled through a somewhat noisy analog signal which would eventually be sent over the inherently unreliable WWW. Spurious commands would occasionally be received by the device making it behave in unintended ways. Occasional network delay or even randomly generated "noise" could abruptly change a command or otherwise change the movements of the dog as if it had a will of its own. The dog leash metaphor allowed us to safely ignore these spurious signals and actions--because we fully expected them.
Max is equipped with a fixed B/W CCD camera. The analog video stream is transmitted via a bidirectional radio transceiver which also provides a back channel for control signals. Essentially the dog broadcasts on channel 52. The video signal is received by another transceiver and fed into the cable TV port of a VCR which provides video-out to a video capture board located on a server. The transceivers have a range of several meters thus allowing control away from fixed network components. This configuration is shown in the figure below.
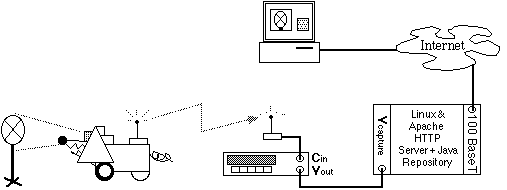
The server hardware is a Pentium-based PC running the Linux operating system and an Apache hypertext transport protocol (http) server. The server is connected to the internet via a 100 Megabit twisted pair Ethernet card. The streaming video software is provided through a custom Java application. Visitors to Max's home page are presented with a configurable "dog's eye view" of the environment and a Java applet providing both gross and fine controls for Max. Multiple users are accommodated through circular Queuing--allowing each user one minute of active control but unlimited passive viewing.
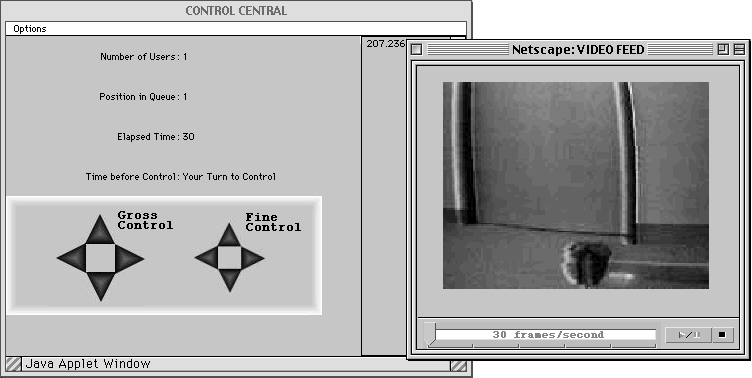

Our initial target audience consisted of young children. We believed that they would be more accepting of the role playing necessary in order to justify the quirky nature of Max. To facilitate this understanding we dressed Max to appear as a stylized dog and built an enclosed arena which allowed an operator to see Max before they attempted to control him. The enclosure was built around a public bench so that Max could interact in a limited way with people who were not involved with Max but just happen to be there. Dozens of children were attracted throughout the day. Inevitably each child caught on to the metaphor and within minutes was skilfully urging Max around the enclosure. To date, children as young as three years old have successfully taken Max for a walk.